EV Charging Stations pose a whole new world of Cybersecurity Risks
30.09.2024With the rising popularity of electronic vehicles (EVs), it makes sense that the number of EV charging stations has skyrocketed.
While this is significant in taking steps away from fuel-powered combustion engines, there are concerns that these charging stations are creating a new landscape of cyber threats that can have a significant impact on everything from the privacy of users to enabling attacks on power grids.
EV charging station ecosystems rely on management apps – both online and web – and unique firmware. Internet highways relay information between these endpoints, dealing with customer data, handling payments, and dishing out resources, meaning these systems are terminally online. The creation of this ecosystem has required innovation, both in building specialized technologies and city planning for implementing accessible charging points for the growing numbers of EV users. This reality has required new approaches to integrated networks that are usable by customers and suppliers alike.
There are a couple of alternative protocols for EVs in the cyberspace of things, but the key player today is the OCPP or Open Charge Point Protocol. OCPP was commissioned in 2009 by the Dutch ElaadNL research foundation, which, among other things, focuses on sustainable charging technologies. OCPP functions as an intermediary between management systems and charging stations. It is a general-purpose communication protocol between different manufacturers and vendors; you could compare it to a USB-C port in that it wants to streamline charging regardless of who made your device.
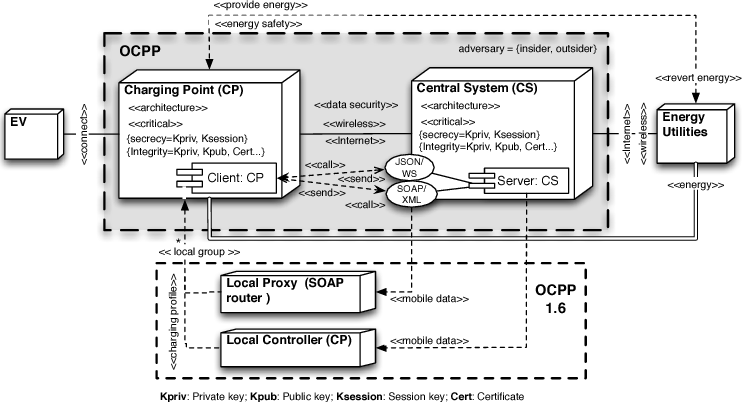
For the network aficionados, this is what OCPP looks like under the hood (version 1.6):
During security research of the OCPP in 2017 by C. Alcaraz, J. Lopez and S. Wolthunden, a set of threat scenarios was recognized in the protocol’s logical function. They recognized elements in the protocol that could be used for Man-in-the-middle, Denial of Energy Service (DoES), and Denial of Service attacks, with various injection attack vectors as well as a vulnerability for signal jamming, data theft of confidential information, and even energy theft and fraud.
In 2021, further research identified a range of vulnerabilities in EV charging ecosystems – not just OCPP, but the intermediary applications – that could be used to perform large-scale attacks with severe impact on the affected charging station, its user, and the power grid. The issue of an EV charging station’s cybersecurity does not just affect individuals but can impact the entire power-supply critical infrastructure.
Yet, these were only possibilities that were identified through research. As of 2017, has anything actually happened?
Yes. Charging stations have experienced cyber-attacks worldwide, but so far these attacks have been limited to cyber-vandalism. Charging stations have been used to display political messages and videos, and in the UK, a number of stations were vandalized to play adult videos on their management screens. A YouTube channel, The Kilowatts, published a video on X (formerly known as Twitter) where a user gains remote control of a charging station’s operating system using a mobile phone.
OCPP has been a topic of multiple National Vulnerability disclosures, of which the majority were ranked as high severity or critical. These disclosures mirrored the vulnerability findings published in 2017, yet worryingly, most of the high-severity cases have been reported as late as 2023.
EV charging stations have not (yet) experienced any of the worst-case scenarios detailed by researchers. However, as reports show, the risks are real and pose a novel cybersecurity threat that can impact critical infrastructure. Luckily, researchers have proposed solutions for addressing these concerns, and more research into EV charging station ecosystems from a cybersecurity perspective is being conducted. OCPP’s vulnerability disclosures go to show that, though research is conducted and issues are found, remediation of these findings is slow; cybersecurity fixes come into play only after something happens, and the implications of the damage that attacks on EV charging stations can cause, the focus on cybersecurity shouldn’t be lost in the joy of building a sustainable, fossil-fuel-free world.
Cyber-resilient Kymenlaakso project is co-funded by European Union via Regional Council of Kymenlaakso from Just Transition Fund (JTF) of the European union. Project duration is 1.9.2023–31.12.2025.
Sources
Alcaraz C., Lopez J., and Wolthunsen S. 2017. OCPP Protocol: Security Threats and Challenges, IEEE Transactions on Smart Grid, vol. 8, pp. 2452–2459, 2017. Saatavilla: https://www.nics.uma.es/pub/papers/AlcarazLopezWolthusen2017.pdf
Nasr T., Torabi S., Bou-Harb E., Fachkha C., Assi C. 2021. Power jacking your station: In-depth security analysis of electric vehicle charging station management systems. Computers & Security, Volume 112, 2022. Saatavilla: https://doi.org/10.1016/j.cose.2021.102511
The Kilowatts. 2023. X (Twitter). Saatavilla: https://x.com/klwtts/status/1619554380591824898
Tik Root. 2023. EV Charger Hacking Poses a ’Catastrophic’ Risk. Wired. Saatavilla: https://www.wired.com/story/electric-vehicle-charging-station-hacks/